A new strain of ransomware nicknamed “Bad Rabbit” has been found spreading in Russia, Ukraine, Turkey and Germany.
Security researchers at ESET have detected Bad Rabbit malware as ‘Win32/Diskcoder.D’ — a new variant of Petya ransomware, also known as Petrwrap, NotPetya, exPetr and GoldenEye.
Bad Rabbit ransomware uses DiskCryptor, an open source full drive encryption software, to encrypt files on infected computers with RSA 2048 keys.
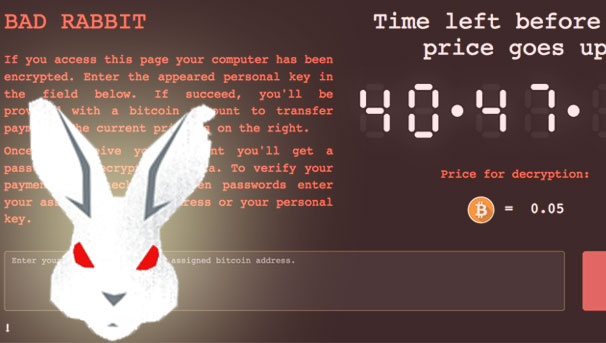
Kaspersky Lab researchers say the cryptography behind this ransomware is called Bad Rabbit; victims are sent to a page with the same title on Tor in order to pay a ransom of 0.05 Bitcoins ($286) to get access to their files back. The note also features a timer counting down from just over 41 hours, telling the user they need to pay within that time or face the ransom going up.
Researchers also note that Bad Rabbit uses attack methods “similar” to June’s Petya attack, but as of yet haven’t confirmed a link with the previous incident, or if it has the capability to spread as widely.
“Based on investigation, this is a targeted attack against corporate networks, using methods similar to those used in the ExPetr attack,” Kaspersky Lab researchers said, adding that one of the methods of distribution is a drive-by attack which drops the malware from compromised websites.
In a Tweet, Kaspersky Lab director of Global Research and Analysis said that some of the compromised websites – including Bakhmut, Ukraine’s municipality website – have been hacked since July this year.
A number of security vendors say their products protect against Bad Rabbit. But for those who want to be sure they don’t potentially fall victim to the attack, Kaspersky Lab says users can block the execution of file ‘c: \ windows \ infpub.dat, C: \ Windows \ cscc.dat.’ in order to prevent infection.
Here are some general tips to raise your defenses against this sort of outbreak:
Kaspersky suggest to disable WMI service to prevent the malware from spreading over your network.
Ditch Flash altogether Fake flash installers and updates only work as a social engineering tactic if you use or want Flash. By removing Flash entirely you not only protect yourself from Flash zero-day holes , but also eliminate the temptation to download fake updates.
Patch promptly Outbreaks such as NotPetya and WannaCry exploited a vulnerability for which patches were already available. Don’t lag behind once patches are available for known security holes – the crooks will be only too happy to take advantage.
Remember your backups Make them regularly, and keep a recent backup both offline and offsite, so you can access it even if your workplace ends up off limits due to fire, flood or some other cause not related to malware.
Don’t make users into administrators When you want to perform administrative tasks, promote yourself to an administrator account, and relinquish those privileges as soon as you can. Network-aware malware like Bad Rabbit can spread without even needing to guess passwords if you already have administrator-level access to other computers on the network.
Most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs.